Take the first step toward security
Don’t wait until it’s too late. Protect your business today.
We deliver a comprehensive platform designed to support the successful digital transformation of your company. Our Platform One solution includes everything you need to ensure seamless application performance within your new private cloud environment.
We leverage modern technologies for cloud infrastructure and automation to provide high availability, flexibility, and scalability. Your IT infrastructure is fully protected against cyber threats thanks to Zero Trust architecture principles and built-in data protection.
Our platform is built on proven open-source tools that combine innovation, transparency, and cost efficiency — delivering a solution tailored precisely to your needs.
Complete IT infrastructure. Secure. Scalable. Yours to command.
The principle of least privilege: Every user, device, or application is granted access only to the resources that are absolutely necessary.
Identity verification: We implement multi-factor authentication (MFA) and continuous identity validation to ensure the highest level of security.
Network segmentation: We separate sensitive systems using software-defined networking (SDN), minimizing the risk of lateral movement by attackers.
Isolation: Applications and services are isolated in containers or virtual machines to enhance security.
End-to-end encryption: We ensure communication confidentiality using TLS/SSL, VPNs, encrypted tunnels, and digital certificates.
Advanced cryptography: We leverage elliptic curve cryptography (ECC) to provide maximum confidentiality for your data.
SIEM: Proactive monitoring setup for log collection and analysis to detect anomalies, potential threats, and technical vulnerabilities.
Security monitoring: Real-time infrastructure protection through IDS/IPS systems and behavioral analysis.
Patch management: Automated software and application updates to reduce risk from known vulnerabilities.
Vulnerability scanning: Regular, automated infrastructure audits to identify weaknesses and protect your systems.
Backups: Regular encrypted backups stored in secure, geographically separated locations.
Disaster recovery planning: A defined Disaster Recovery Plan (DRP) ensures fast recovery in case of cyberattacks or system failures.
We protect your data and systems using Zero Trust architecture, advanced encryption, network segmentation, and other proven security practices such as VPN implementation.
With automated threat detection, your sensitive information stays protected — simply, reliably, and without compromise.
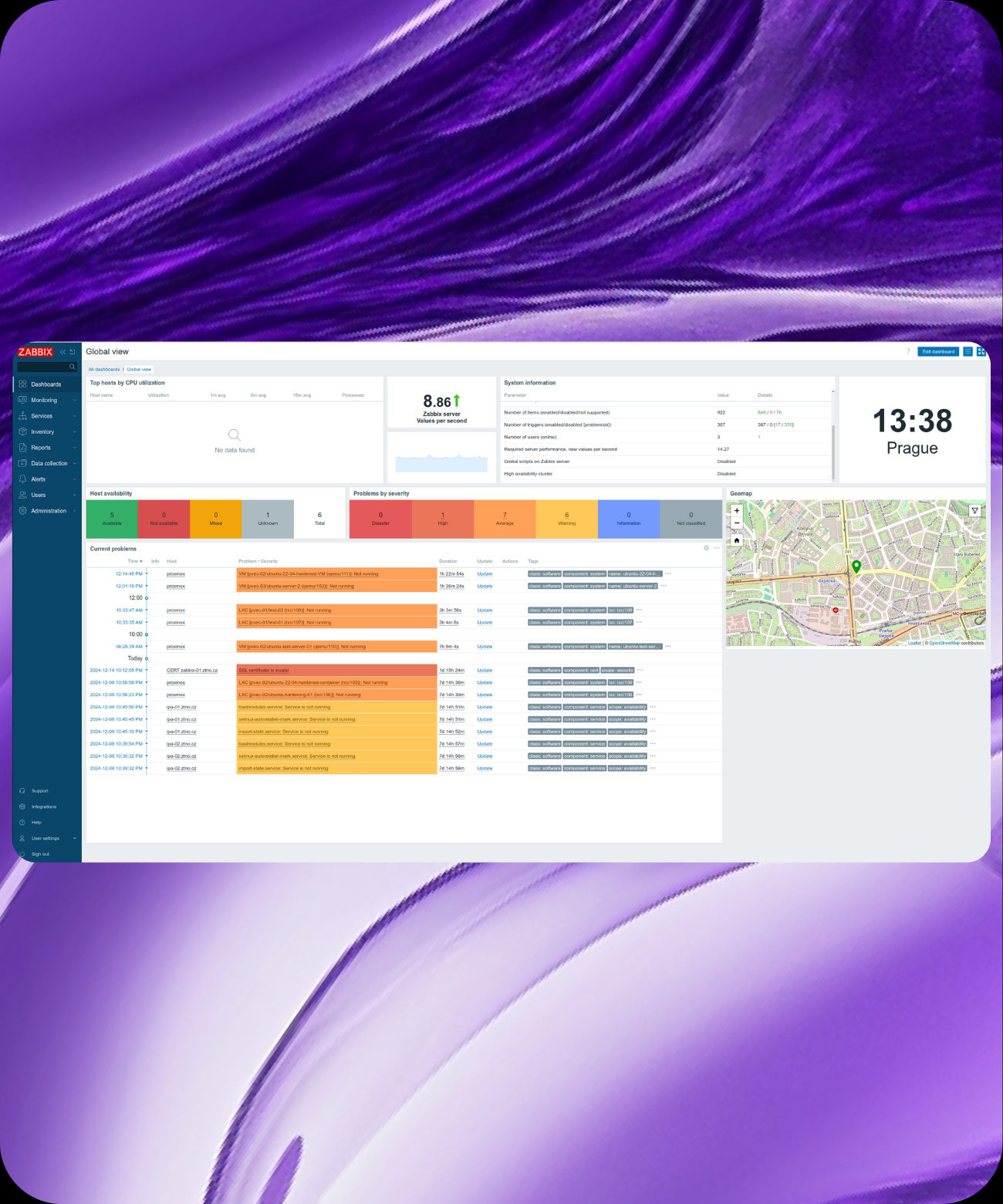
Simplicity, efficiency, and scalability. Platform One solution brings together all critical components of your IT environment into one cohesive system. From virtualization, storage, and networking to automation, monitoring, and security — everything is fully integrated and interconnected.
This makes management easier, operations more efficient, and costs lower. With our solution, you save time, boost performance, and gain the flexibility your business needs to grow.
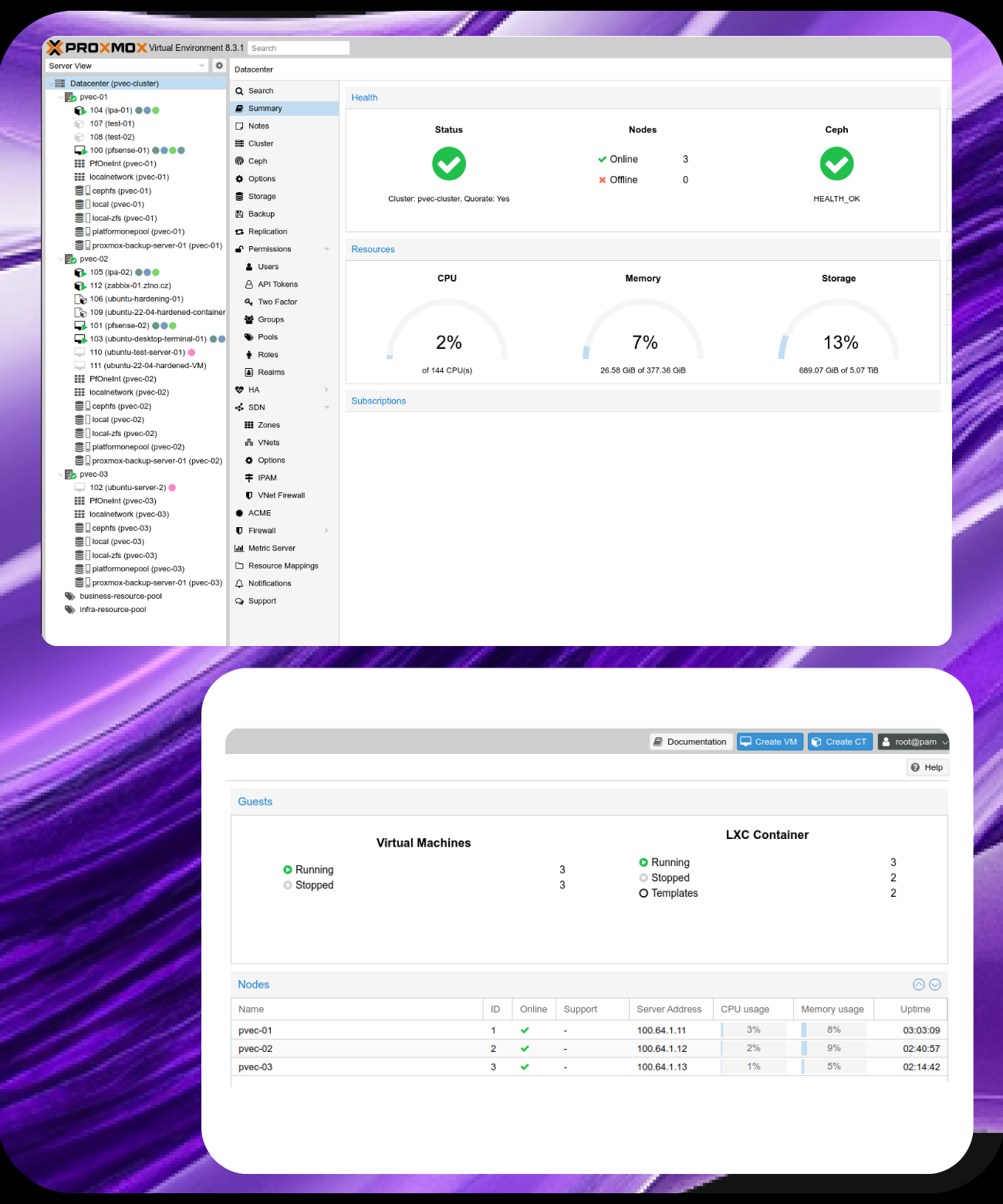
Choose the deployment model that best fits your needs. Run our services on your own infrastructure — or leverage our secure server platform.
Whichever option you choose, we guarantee high performance, maximum security, and full support.
Our flexible solution adapts precisely to your requirements.
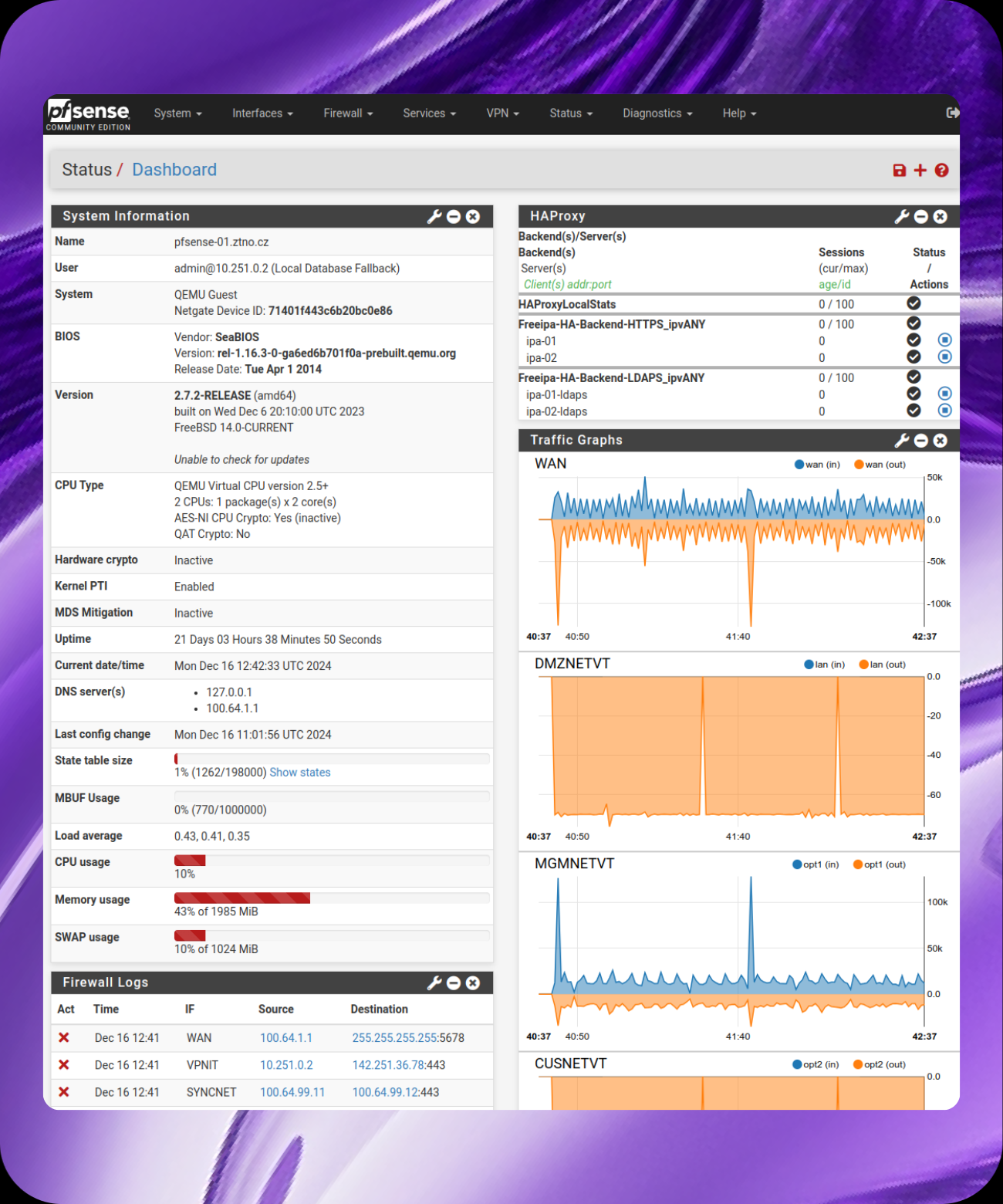
Our solution enables smooth integration and synchronization of tools focused on managing and securing your IT infrastructure. This integration supports automated security enforcement, real-time system monitoring, and threat detection.
In addition, it covers full IT Service Management (ITSM), enabling efficient handling of services and incidents across the entire IT environment.
As a result, you gain complete control over your infrastructure, faster response to change, and maximum operational efficiency.


















Break free from outdated systems. Step into a world where security comes first. With modern technologies and proven best practices, we’ll build an IT environment that’s resilient to threats and ready to meet your future needs.
Security isn’t just a goal — it’s an ongoing process that drives your business forward. Get ready for a new era of IT: safer, more flexible, and more efficient.
I. We perform a detailed audit of your infrastructure and evaluate the criticality of your applications, systems, and data.
II. We identify key risks and define priority areas to maximize your security posture.
III. Together, we assess your business continuity goals to ensure resilience under any conditions.
I. We present a detailed migration strategy for your infrastructure and applications to optimize performance and strengthen security.
II. We fine-tune the plan with you to ensure zero disruption to your business operations.
III. Upon approval, we validate all requirements and prepare everything needed for a smooth rollout.
I. We allocate dedicated hardware and prepare it for full solution deployment.
II. We execute all pre-migration steps on both sides to ensure a seamless transition.
III. We build and test the entire solution in parallel with your existing infrastructure.
IV. Finally, we carry out a secure and controlled migration as per the agreed plan.
I. Security is not a one-time event. We continuously monitor your infrastructure, detect potential threats, and respond rapidly.
II. We adapt the system to evolving threats — and to your changing business needs.
III. We ensure your environment remains stable, secure, and ready for the future.
Our pricing combines flexibility, transparency, and reliability — so you can focus your time and resources on growing your business.
Have questions about our solution? Here you'll find answers to the most common queries — and learn how we can strengthen your company’s security and simplify the management of your IT infrastructure.
Yes — we’re ISO ready. With our solution, you can achieve ISO certifications with ease and without unnecessary complexity.
We provide the technological foundation needed to meet the requirements of the following ISO standards:
We also provide a robust IT foundation for the following standards:
Yes, absolutely. We’ll review your needs and propose the best setup as part of our solution assessment. In many cases, we recommend keeping certain services in their current environment — for example, email systems hosted by providers like Google Workspace or Microsoft 365.
We offer comprehensive support tailored to your needs. Responsibilities and competencies can be flexibly shared between your team and ours. If you require a higher level of service, we can provide an Enterprise Support Plan that includes 24/7 priority support and a dedicated account manager.
We don’t offer a publicly available online demo at the moment — but we’d be happy to give you a personalized walkthrough. We’ll show you how our platform works in detail and explain how we can collaborate to help you achieve your goals.
Extremely secure. We use modern, high-grade encryption based on elliptic curve cryptography (ECC).Our platform is protected by multiple layers of security, including fully segmented networks and access via multiple independent VPN tunnels — in accordance with the segregation of duties principle. Proactive monitoring is in place across the entire infrastructure. All system access is strictly controlled and approved by you. Backups are encrypted and stored in separate geographic locations to ensure maximum data protection.
The possibilities are virtually unlimited — the key to success lies in properly designed application architecture. We bring deep expertise in this area and are happy to discuss your systems’ architecture with you, not just from the infrastructure perspective, but also in terms of long-term performance, scalability, and security.
Don’t wait until it’s too late. Protect your business today.
